Google Drive API (oauth 2.0) Upload Files Java
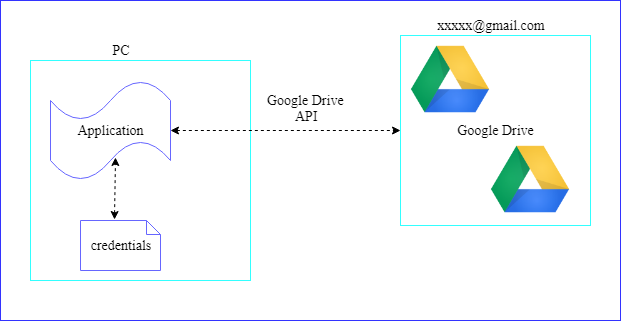
Upload Files Java Google Drive Create Credentials Follow previous : Create Credentials Add Dependencies to Maven Project 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 <!-- https://mvnrepository.com/artifact/com.google.apis/google-api-services-drive --> <dependency> <groupId> com.google.apis </groupId> <artifactId> google-api-services-drive </artifactId> <version> v3-rev105-1.23.0 </version> </dependency> <!-- https://mvnrepository.com/artifact/com.google.api-client/google-api-client --> <dependency> <groupId> com.google.api-client </groupId> <artifactId> google-api-client </artifactId> <version> 1.23.0 </version> </dependency> <!-- https://mvnrepository.com/artifact/com.google.oauth-client/google-oauth-client-jetty --> <dependency> ...


