Cross-site Request Forgery protection in web application
Synchronizer Token Pattern
State Changing Operations Requires Secure Random Token to prevent CSRF Attacks.
Characteristics
- Unique per user session
- Large Random Value
- Generated By Cryptographically secure random number generator
- The CSRF token is added as a hidden field for forms or within the URL if the state changing operation occurs
- The Server rejects if CSRF token validation Fails
About Application
- Java Based Web application which has simple hard coded login page
- User login to the application with user name "asd" and pssword "123"
 |
| LoginForm |
- Upon successful login session id generates and store as a cookie in browser
 |
| Store Cookie |
 |
| Session Cookie |
- At the same time Generates CSRF token and store in server side
 |
| Generate CSRF Token |
 |
| Generated CSRF Token |
Method GenerateCSRFToken
 |
| Method GenerateCSRFToken |
- The End Point Accepts the HTTP POST requests and respond with the CSRF token.The endpoint receives the session cookie and based on the session identifier, return the CSRF token value
- There is another HTML Form which invokes the endpoint for obtaining the CSRF token created for the session via JavaScript an Method is POST.Once the page is loaded, modify the HTML form’s document object model (DOM) and add a new hidden field that has the value of the received CSRF token.
 |
| Script |
 |
| From |
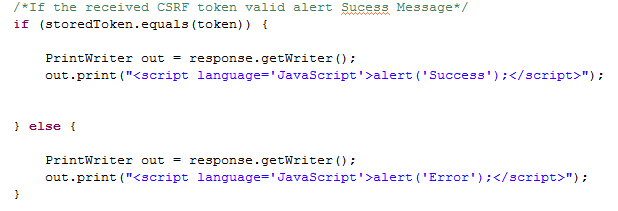
- Once the HTML form is submitted to the action, in the server side, extract the received CSRF token value and check if it is the correct token issued for the particular session. If the received CSRF token is valid, show success message. If not show error message.
 |
| Extracted Token |
 |
| Success Message |
References













Comments
Post a Comment